S1.0-Introducing Google Workspace DLP (Google Drive)
- April 26, 2023
- by
- Nawrin
Google Drive Data Loss Prevention (DLP) is a feature that helps organizations protect their sensitive data in Google Drive. DLP is a set of tools and techniques that helps identify and classify confidential or sensitive data and ensure unintended exposure of sensitive information.
Google Drive DLP offers a wide range of predefined detectors for sensitive data such as credit card numbers, social security numbers, bank account numbers, and more. It also allows you to create custom detectors based on patterns or regular expressions that match your organization’s unique data. Once detected, the DLP policies can trigger a range of actions, such as adding a badge on the document that has sensitive information, sending an alert to the administrator, warning users on external sharing of sensitive information, blocking on external sharing a file that contains confidential information and so on.
In addition to preventing sensitive data leaks, Google Drive DLP also provides administrators with visibility into how their organization’s sensitive data is being used, allowing them to make informed decisions about how to better protect that data. By using Google Drive DLP, organizations can ensure that they are taking a proactive approach to protecting their sensitive data in the cloud. It also allows controlled sharing for members of a domain, organizational unit, or group.
Features of Google Drive DLP
- To acquire information on sensitive files uploaded by users, audit the usage of sensitive content in Drive that users may have already shared. It provides total visibility into how much sensitive data exists, where the data exists, and who owns that sensitive data.
- End users can be warned not to share sensitive content outside of the organization’s domain.
- Prevent/Block sharing of sensitive data with external users.
- Alert administrators or others about any policy violations or any DLP incidents.
- Investigate details of an incident.
Google Drive DLP Workflow
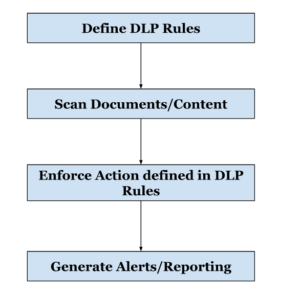
Step 1 : Define DLP Rules
To secure sensitive content, DLP rules must first be created. This rule should include the name, definition, scope, the type of data to be scanned for, the type of detector to be used (predefined or custom created), and when any action to be taken once the rules are implemented.
Step 2: Scan the documents/contents
Once the rules are active, they scan the documents residing in the scope of the rules. It usually includes both My Drive and Share Drives of an organization. The scope can be organization wide or it can be limited to specific members of a domain, organizational unit, or group.
Step 3: Enforce Action defined in rules
When the scanning completes, the action described in the rules is enforced – adding a badge/label if the document includes sensitive information, warn the user about sharing specific documents, or even prohibit users from sharing externally.
Step 4: Generate Alerts/ Reporting
Once an action has been taken, it can be viewed from logs events. Admin alerting can also be configured to notify the administrator or anybody else if a rule is violated. Ex: Generate an admin alert when a user tries to send a document that has 100 Social Insurance Number.
NB: Drive DLP and Chat DLP are available to Cloud Identity Premium users who also have a Google Workspace license.



