
Know about Cyber Kill Chain !!!
- January 15, 2023
- by
- Nawrin
The Cyber Kill Chain refers to the steps that attackers take to infiltrate the system and exfiltrate the data. The cyber kill chain, derived from a military model developed by Lockheed Martin in 2011, is a step-by-step approach to understanding a cyberattack with the goal of recognizing and preventing malicious activity. There are a total of seven stages of this chain.
PHASE 1: Reconnaissance
The attacker obtains information about the target and the attack strategy at this phase. In doing so, potential targets are scouted, weaknesses are found, potential entry points are investigated, email addresses are harvested, and other information is gathered. Automated scanners are used by hackers to find systemic weak spots. Identifying an attack entry point, entails scanning firewalls, intrusion prevention systems, and other security systems. The attack will be more sophisticated and successful the more information the attacker gathers during this stage.
Counter Measure:
-
- Paying close attention to analyzing website visitor logs
- Using the current browser analytics
- Prioritizing defenses based on specific technologies or browsing behaviors that are unique to reconnaissance activity
PHASE 2: Weaponization
The attacker advances to the weaponization phase of the Cyber Kill Chain after conducting reconnaissance and obtaining all essential data about possible targets. The attack vector that will be employed in the cyberattack. This could include malware that allows for remote access, ransomware, or a virus or worm that can take advantage of vulnerabilities identified during the reconnaissance phase.
Counter Measure:
-
- Analyze malware, paying particular attention to how the payload was created.
- Gather data (files and metadata) for the next digital forensics.
- APT (advanced persistent threat) campaign identification
- Training on security awareness
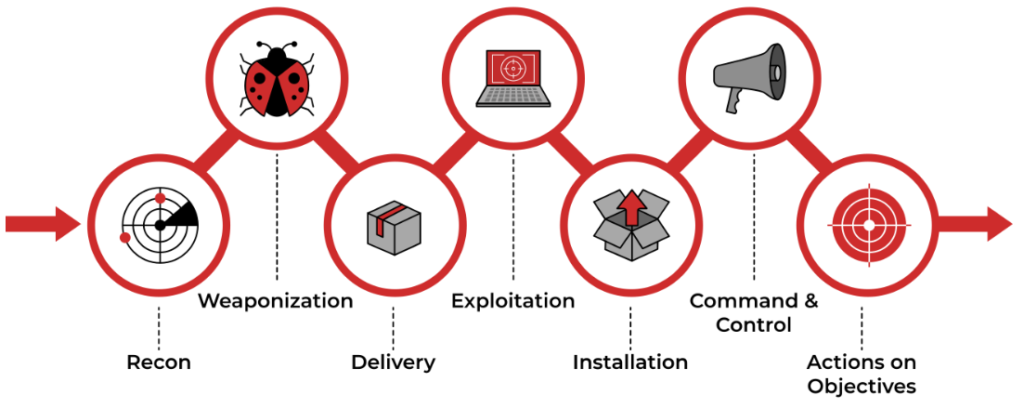
PHASE 3: Delivery
The attack vector is then disseminated by the attackers using a channel like phishing emails with malware attachments and clickbait subject lines, or by breaking into the target’s machine or network. The attacker has now formally begun an attack against the target.
Counter Measure:
-
- Analysis of the delivery method
- Recognize the effect of target systems
- Knowing the roles and duties of the individuals on the targeted servers as well as the sensitive data they have access to
- Examining the time of day the attack started
- Web and email data are being gathered for forensic reconstruction. One must be able to determine when and how delivery started, even if an intrusion is discovered after the fact.
PHASE 4: Exploitation
The target’s systems are then used to run the malicious code. Attackers can access the target’s systems by breaching the perimeter and further exploit them by installing tools, running scripts, or changing security certificates. Exploitation attacks include but are not limited to, scripting, dynamic data sharing, and local job scheduling.
Counter Measure:
-
- Employee email testing and user awareness training
- Construct secure source code
- Conduct reliable vulnerability scanning and penetration testing on a regular basis.
- Admin privilege restrictions and custom endpoint rules are examples of endpoint hardening techniques that prevent the execution of shellcode.
- Auditing endpoint processes to forensically identify the source of the exploit
PHASE 5: Installation
The attack vector is placed on the target’s computers during the installation step, which follows the exploitation phase. Attackers may build back doors into the target’s systems or networks during the installation stage, enabling them to keep gaining access even if the original point of entry is found and secured.
Counter Measure:
-
- Apply NIPS/HIPS and NIDS/HIDS appropriately.
- Recognize the malware’s level of privilege
- Alerting or obstructing popular installation routes
- Auditing endpoint processing to find unusual file creations
- Know the development date and time of the malware
- Recognize when malware was compiled
PHASE 6: Command and Control
During the command and control phase, cybercriminals communicate with the attack vector that has been successfully installed onto a target’s network to give instructions to cyberweapons or tools to accomplish their goals. Threat actors may also move laterally during the command and control phase in order to avoid detection and set up other points of entry.
Counter Measure:
-
- Discover C2 infrastructure through malware analysis
- Limit the number of entry points for infrastructure. Reduce the number of internet points of presence on your network and use proxies for all sorts of traffic to harden it (HTTP, DNS)
PHASE 7: Actions on Objective
After creating cyberweapons, putting them on a target’s network, and taking over that target’s network, cybercriminals start the final phase of the cyber kill chain. Despite the fact that the objectives of cybercriminals vary depending on the type of cyberattack, some examples include using a botnet to disrupt services with a Distributed Denial of Service (DDoS) attack, disseminating malware to steal sensitive data from a target organization, and using ransomware as a tool for cyber extortion.
Counter Measure:
-
- Create an incident response plan with executive involvement and a communications strategy.
- Detect lateral movement, the theft of credentials, and the exfiltration of data
- All alerts receive immediate analyst reaction
- Pre-deployed forensic agents at endpoints for quick triage
- Network package capture for active recreation
- With the assistance of subject-matter experts, assess the damage.




